Can’t-Miss Takeaways Of Tips About How To Prevent Replay Attack
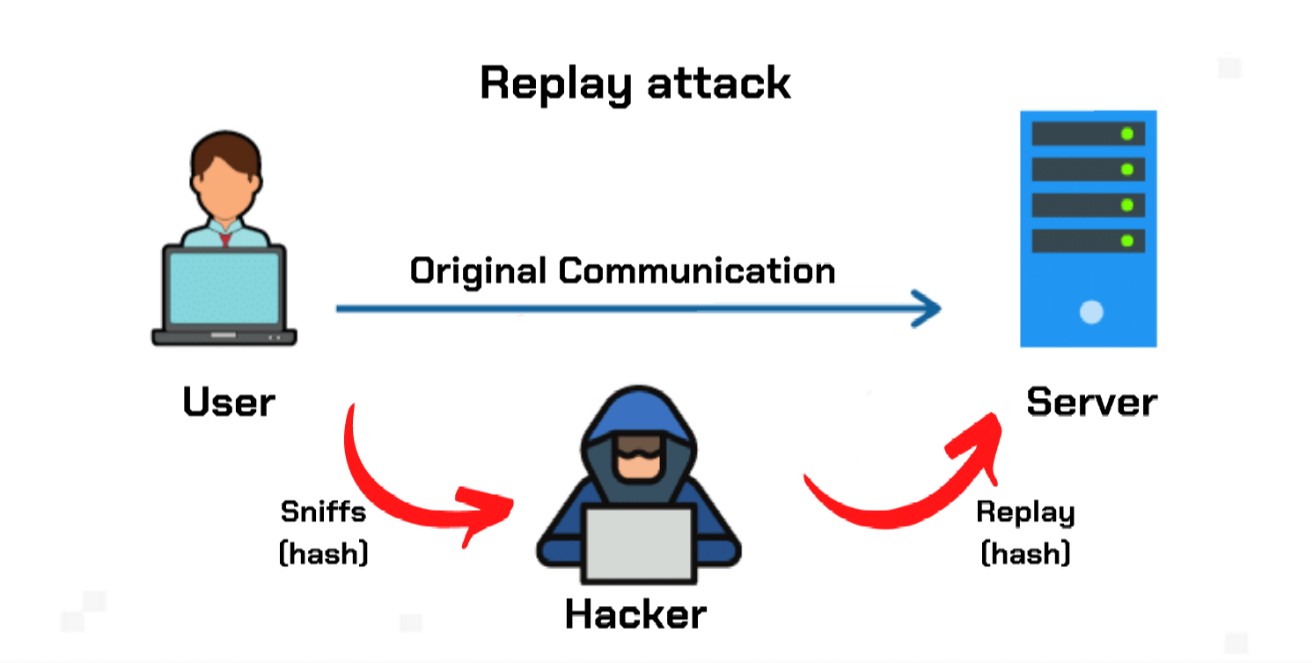
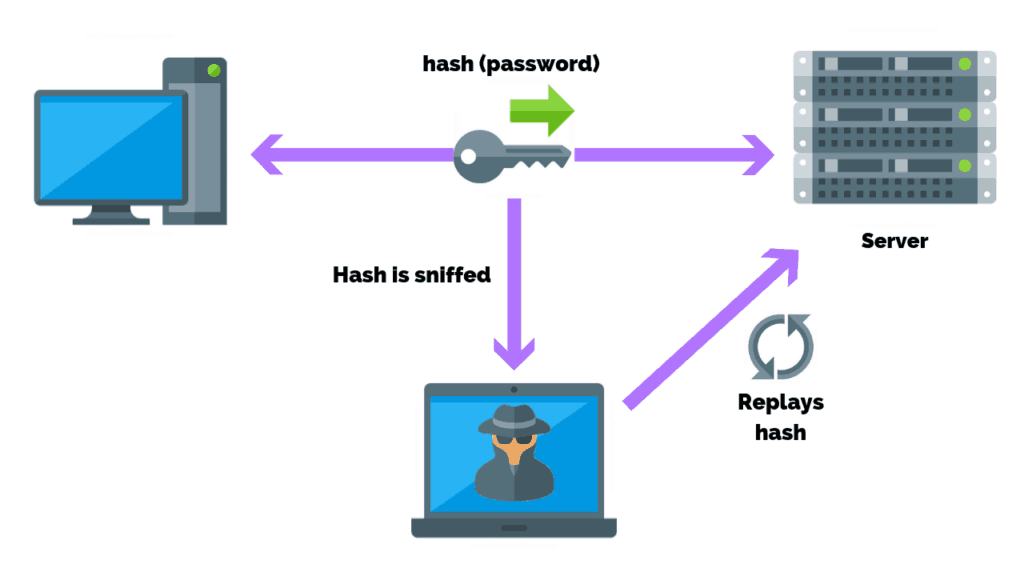
Because the hacker doesn’t need to read or decipher the encrypted.
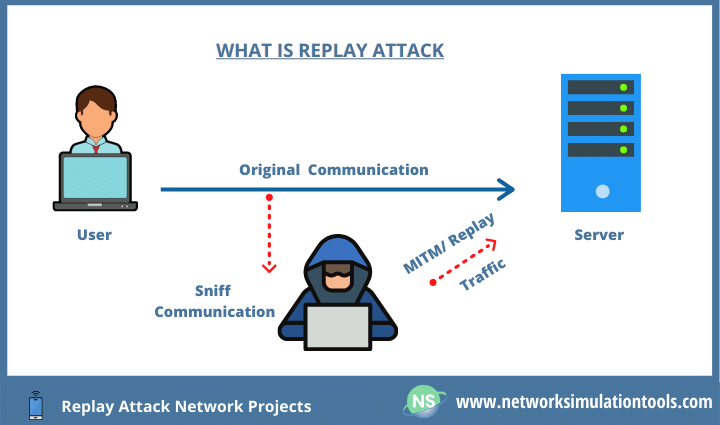
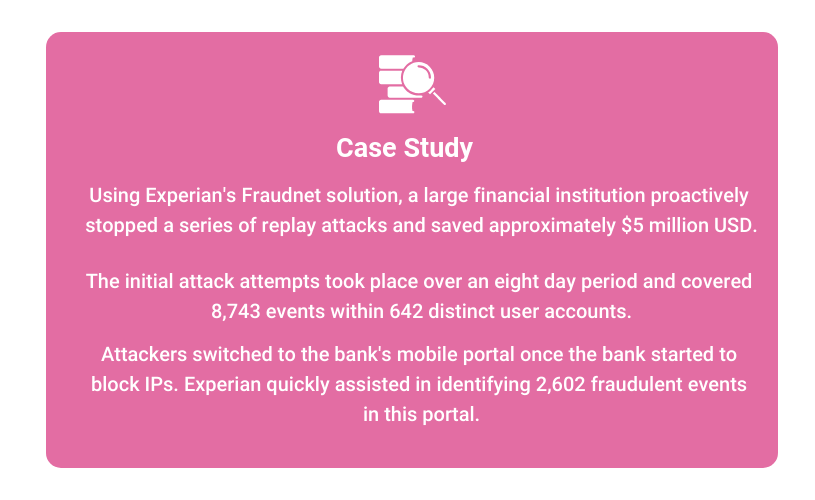
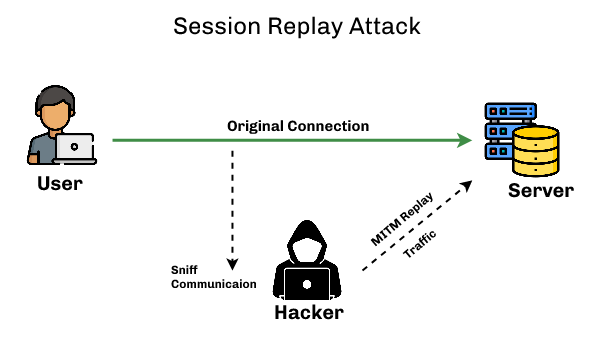
How to prevent replay attack. While it is ideal to stop the attack from happening at all, the next best thing is to limit the damage it can do to your system. Up to 80% cash back 🔒 avoid unsecured public networks: Simply preventing a replay attack is not enough.
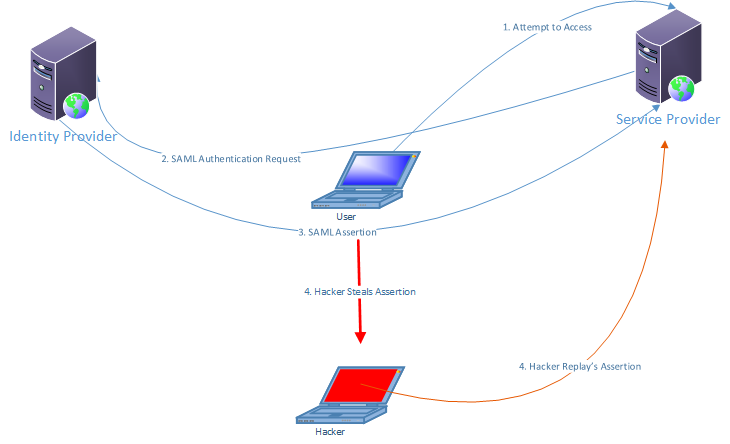
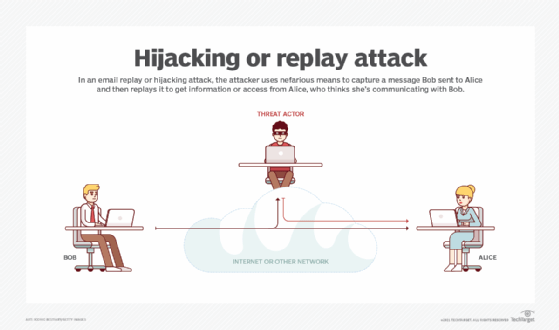
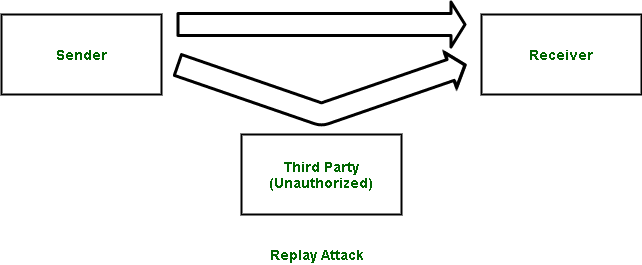
Replay attacks work because hackers can steal something you're using right now and send it again without changing a thing. Prevention from replay attack : How to prevent replay attacks at the moment, most blockchains have installed security protocols to prevent this type of attack, including 2 notable tools:
So, what will you do to stay safe?. Basically, replay attacks can be prevented by implementing digital cryptography or preventing people from logging into online accounts multiple times using the same password,. How to stop replay attack.
Stopping a replay attack all he or she has to do is capture and resend the entire thing — message and key — together. To counter this possibility, both sender and receiver. This article is intended to bring awareness to the.net web service developers about the replay attacks and to learn about measures to secure the web services they build.
8 ways to prevent replay attacks require a session key. Session keys can only be used once within a specific time period to encrypt and decrypt data. To stop replay attacks from occurring, you can do a few things.
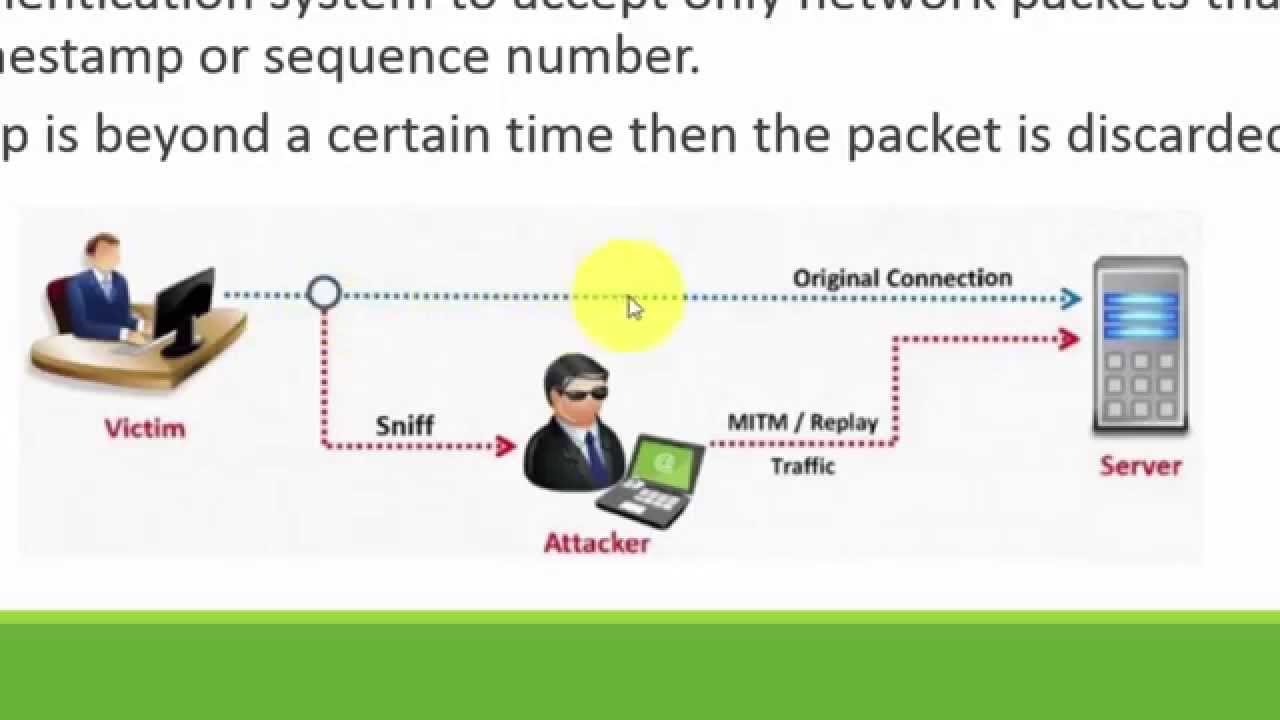
The session key is generated at random at the time. To block this attack, you must make theft harder,. If you really don't want to store any state, i think the best you can do is limit replay attacks by using timestamps and a short expiration time.






![Replay Attacks - Kerberos: The Definitive Guide [Book]](https://www.oreilly.com/library/view/kerberos-the-definitive/0596004036/httpatomoreillycomsourceoreillyimages2077818.png)